80% of ransomware attacks are rooted in mistakes made by a business in configuration, according to a recent article by Microsoft. Think about that for a moment: four fifths of all the damage caused by ransomware to businesses over the last few years could quite possibly have been cleanly avoided without anything more than having the correct configuration being in place. I recognise that this is an easy statement to make, and it is headline grabbing as well, but stay with me.
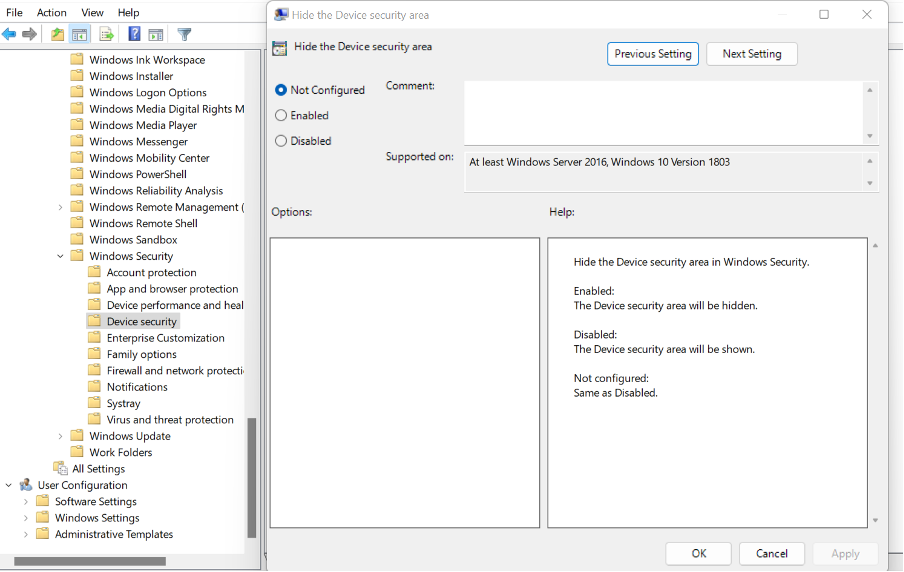
Typically, certainly in the case of most Microsoft products and services, you use Active Directory Group Policy Objects (GPO) to deploy and manage configuration on your managed devices, be it the user experience, device behaviour or security configuration. But GPO isn’t actually very good at what it tries to do, sure it is from the product vendor and forms the best way to maintain a common and approved configuration, but it is also slow, hard to troubleshoot, cryptic with double negatives in the descriptions, has no true reporting or feedback, and can only be used in well-connected environments. It has always had shortcomings and quirks, but primarily it was never designed for the world of WFH, BYOD, VPN, ZTNA or any other of the initialisms that we use every day.
My personal pet hate with enforcing configuration via GPO is the way that you set a configuration into policy and must cross your fingers and hope that: a) it has been applied to every targeted device – and only those devices that are intended and, b) the policy item remains enforced permanently. This leads to a potential scenario where a policy item was not applied or it was subsequently circumvented or removed, and this outcome can leave your environment wide open to risk as it only takes 1 incorrectly configured device to leave your environment exposed.
But love it or hate it, GPO is here to stay, and it is not going to change anytime soon.
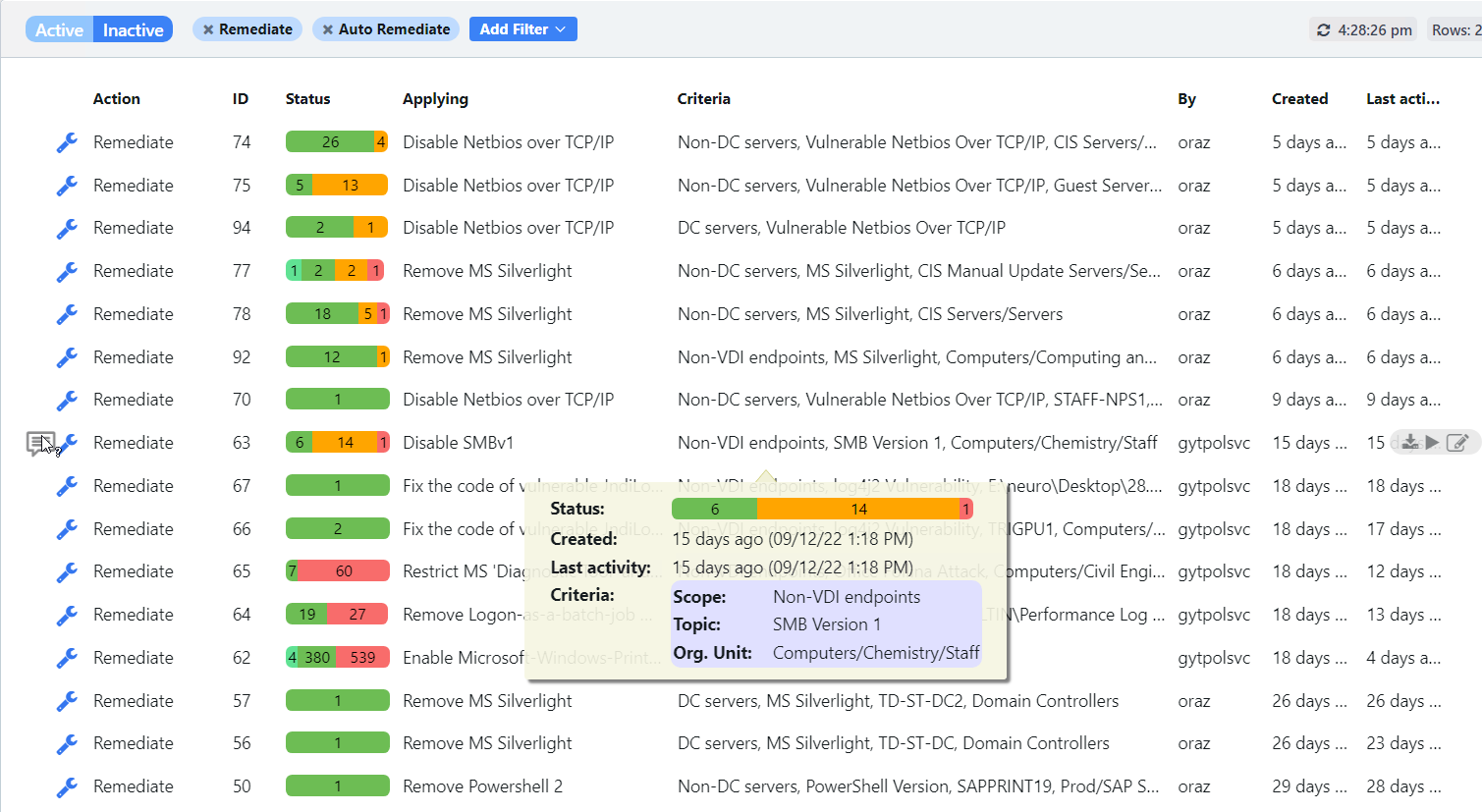
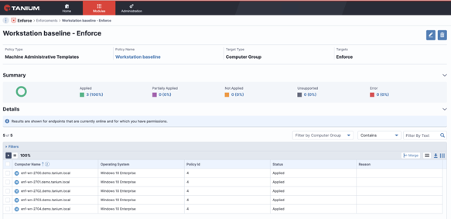
When Tanium released their Enforce module, I was excited with the ability to finally apply policy, see where policy failed to apply or where it was circumvented, and also apply the policies items across all devices globally with no need to follow Active Directory hierarchy – all in real-time. It changed the way that policy is managed and deployed across an environment.
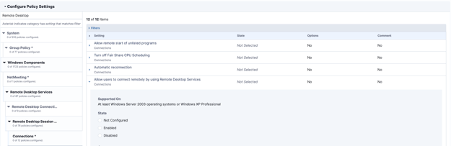
With Enforce you can configure all machines policy, combined with your disk encryption and Windows Defender policy, from a single console and then immediately apply it to all managed devices, where they are on-premise, off-premise, cloud, hosted, datacentre, or even across all devices regardless of whether or not they are in the same Active Directory Domain/Forest; it is truly centralised policy management. And because of the real-time nature of the Tanium platform, you finally have that visibility that was missing. Whilst it is not perfect, Enforce is a superb solution to this problem, and when compared with the other facets on the Tanium platform it is a solution that is very hard to disregard.
But what about misconfigurations? What about the devices where policy was applied, but it wasn’t the correct configuration, or doesn’t map to a best practice? In this scenario your policy is working just fine, the problem instead is that the wrong configuration is being deployed, and once again you have no idea that this situation even exists until something happens.
In my opinion a misconfiguration is so much worse than no configuration because with a misconfiguration you can led to believe that you are protected whilst blissfully unaware that there is an exploitable vulnerability in your network; it’s a false sense of security in a dangerous world. And this leads back to my opening sentence in this post, that 80% of all ransomware events were due to misconfigurations.
The answer to this quandary already exists, I am not hypothesising about a gap in the tech industry that leaves businesses wide open and vulnerable, and with no solutions available; this 80% ransomware scenario of misconfiguration that I describe can be addressed today, and with minimal effort.
The answer to this quandary already exists, I am not hypothesising about a gap in the tech industry that leaves businesses wide open and vulnerable, and with no solutions available; this 80% ransomware scenario of misconfiguration that I describe can be addressed today, and with minimal effort.
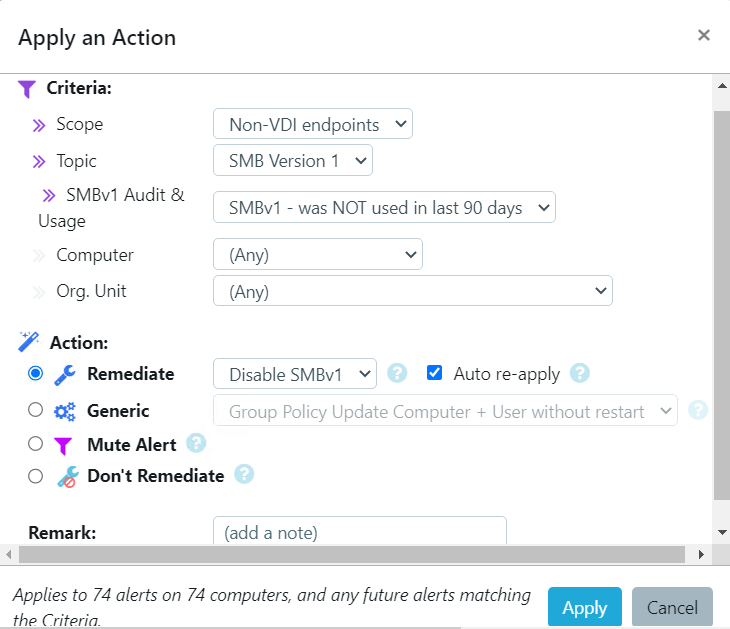
Microsoft for Startups Tom Davis recently described GYTPOL as “one of the most exciting cyber-startups I have come across in recent years”, and I could not agree more. It is a solution that can answer all the points I made above, more. With GYTPOL, as you apply policy across your environment it is inspecting it to make sure that it is applied to a device, and importantly that the configurations deployed are correct and that they match best practices, standards, recommendations, and everything else. And not only that, but they have also taken the “big button” approach to make remediation immediate and easy; you don’t need to go back and trawl through settings, layers of policy or anything else, you just hit the button for an immediate response.
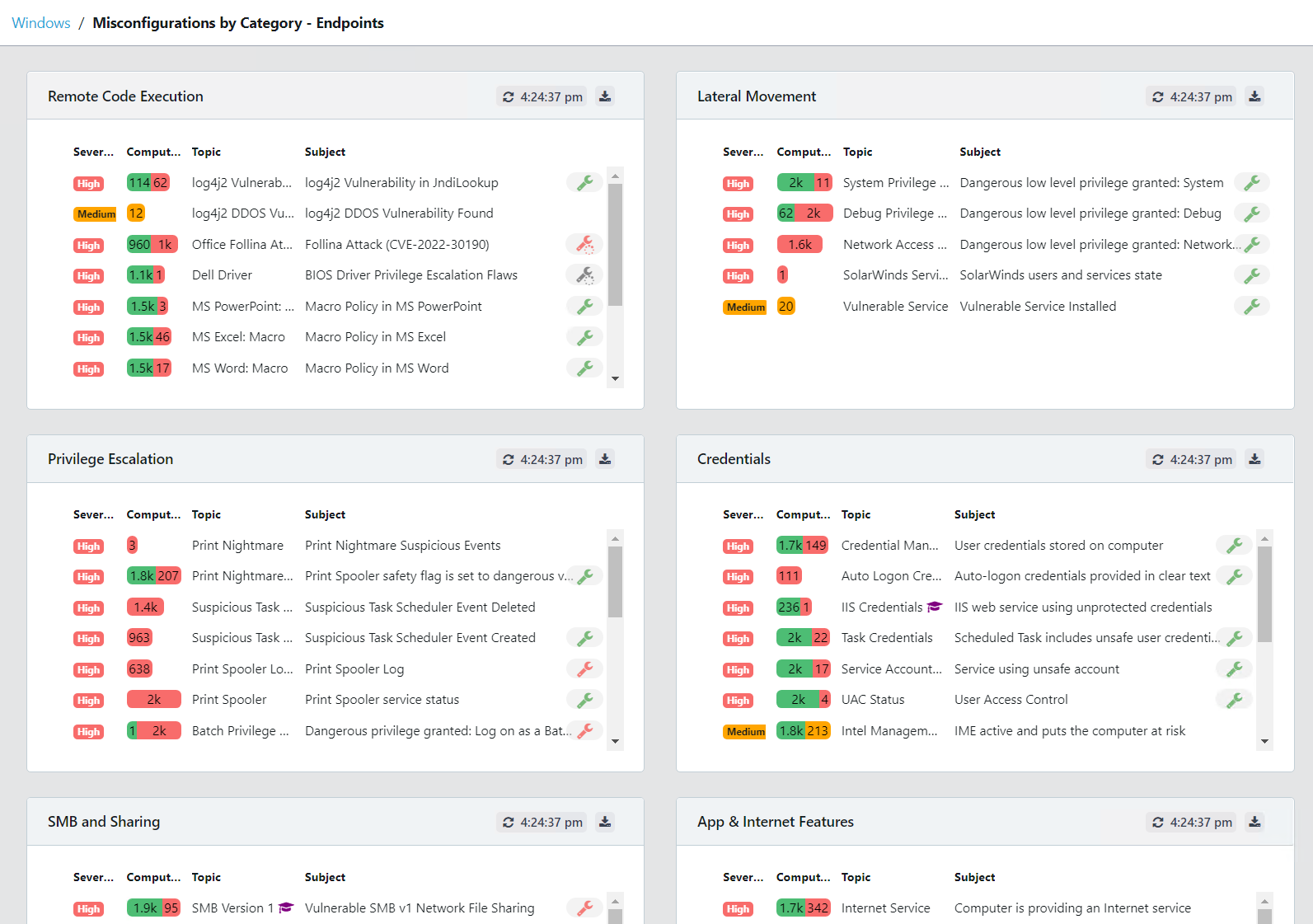
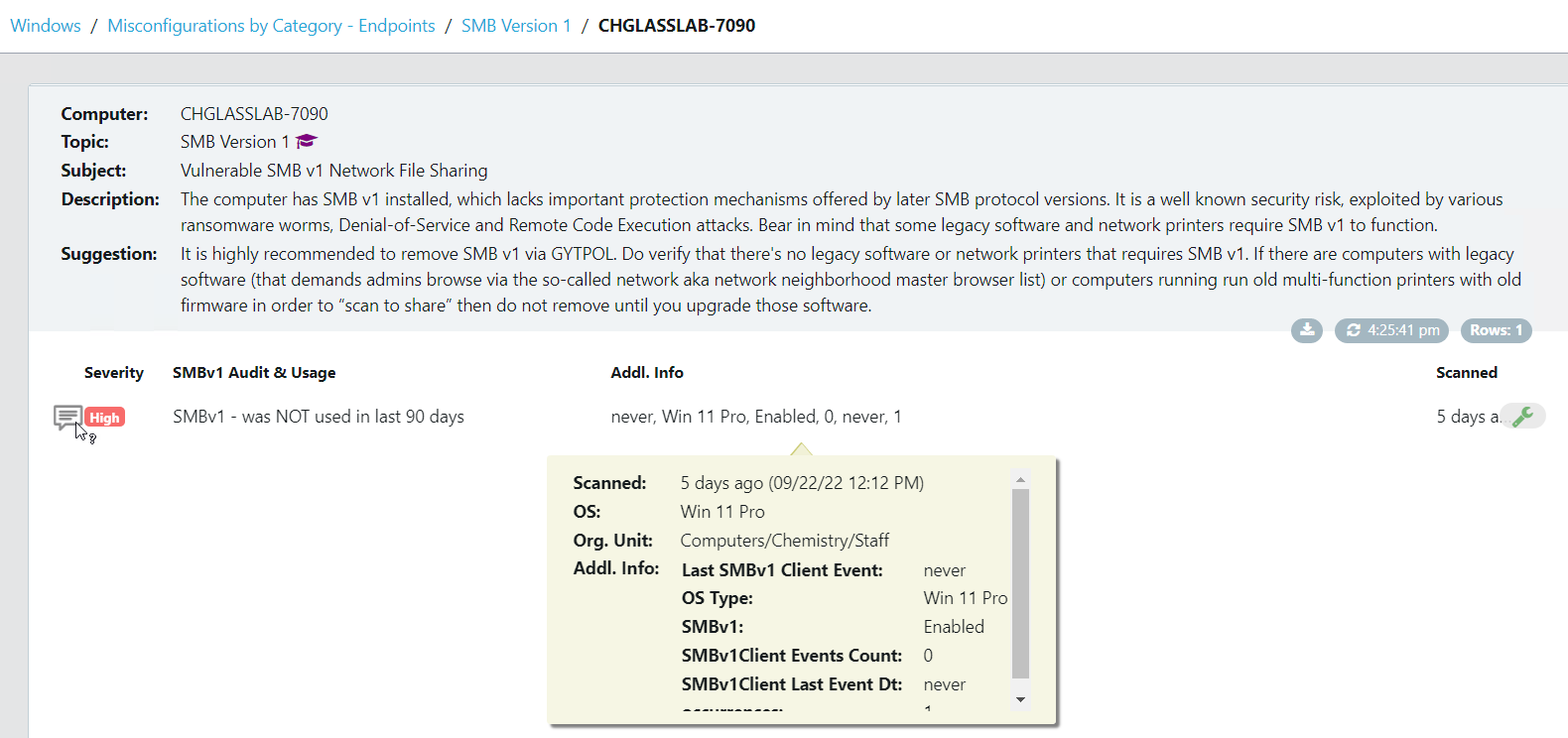
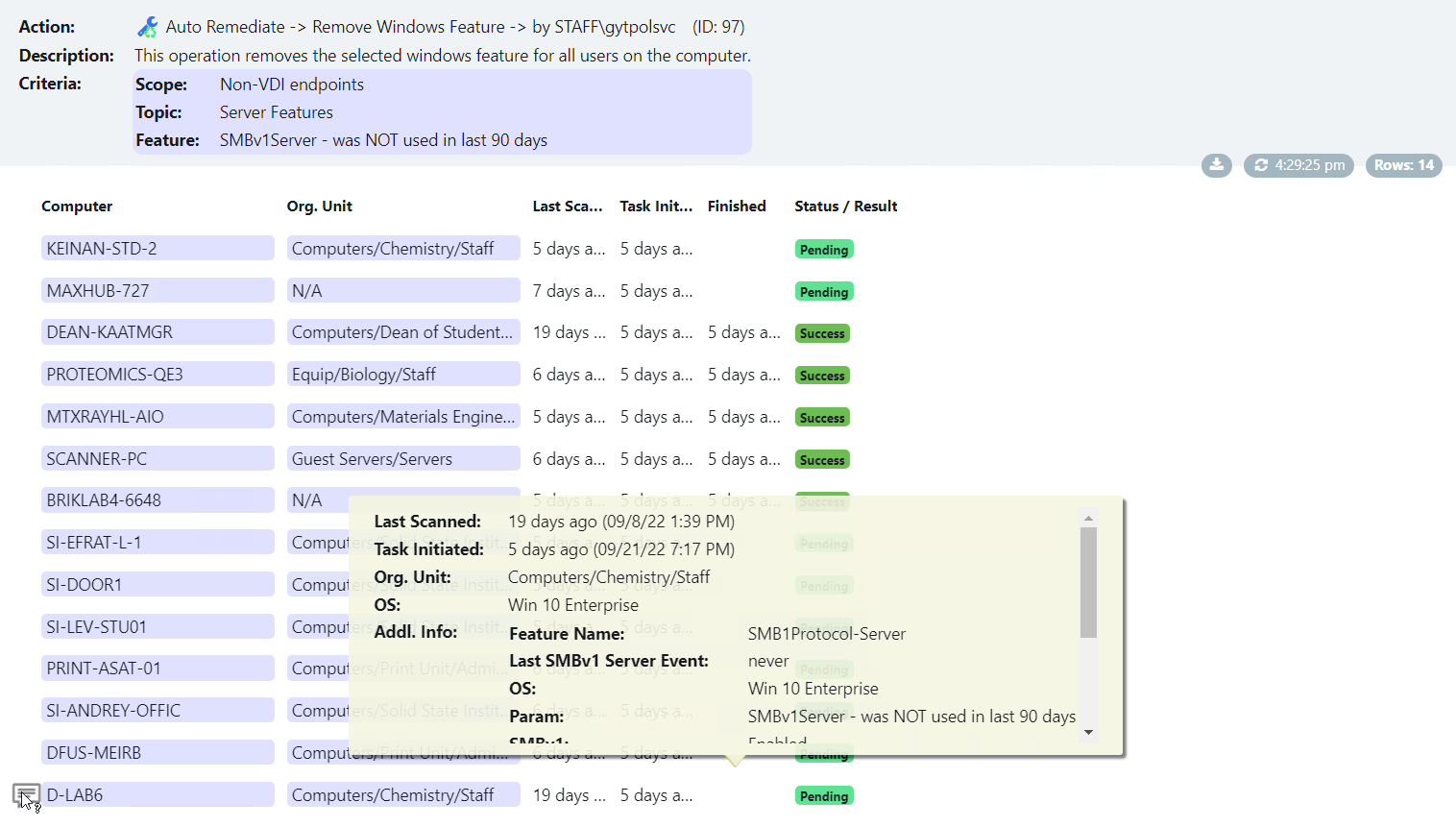
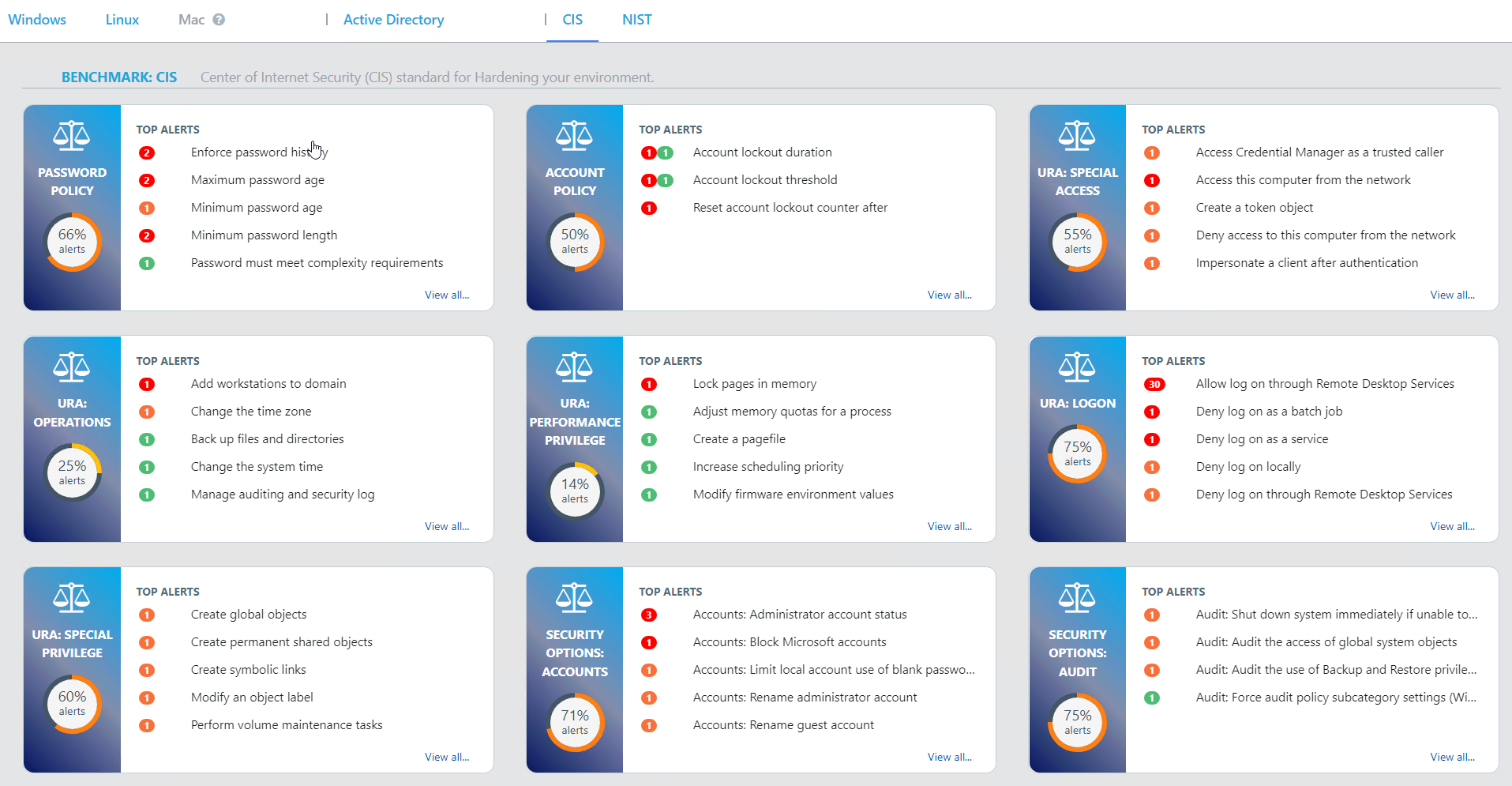
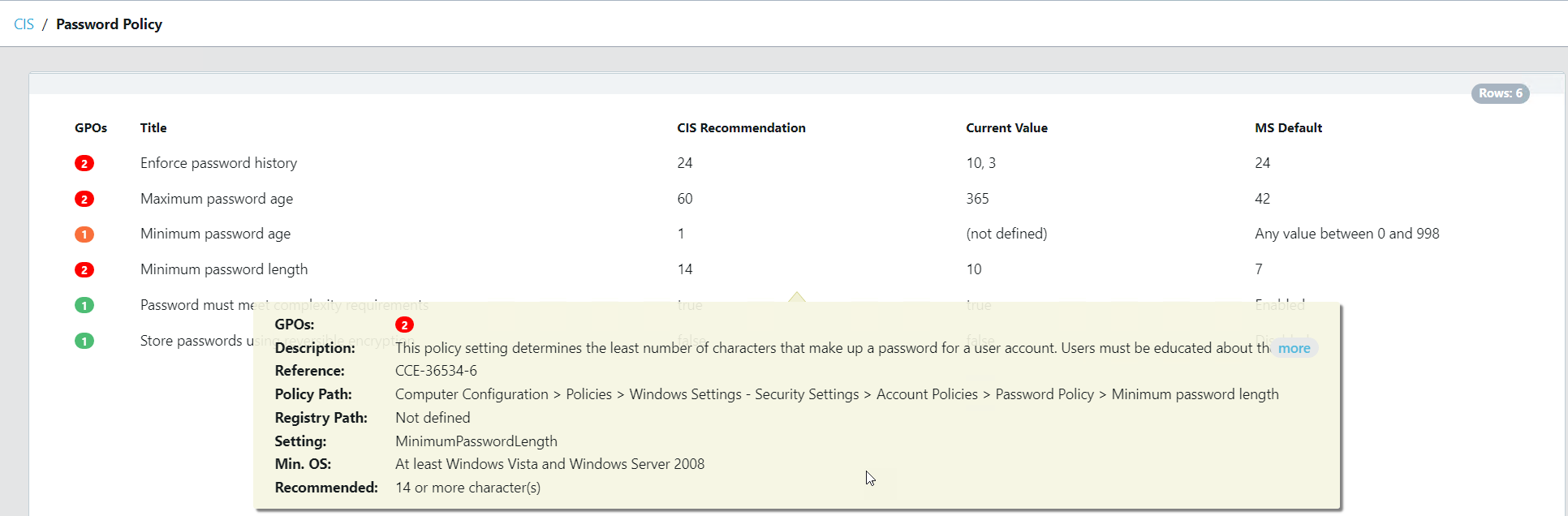
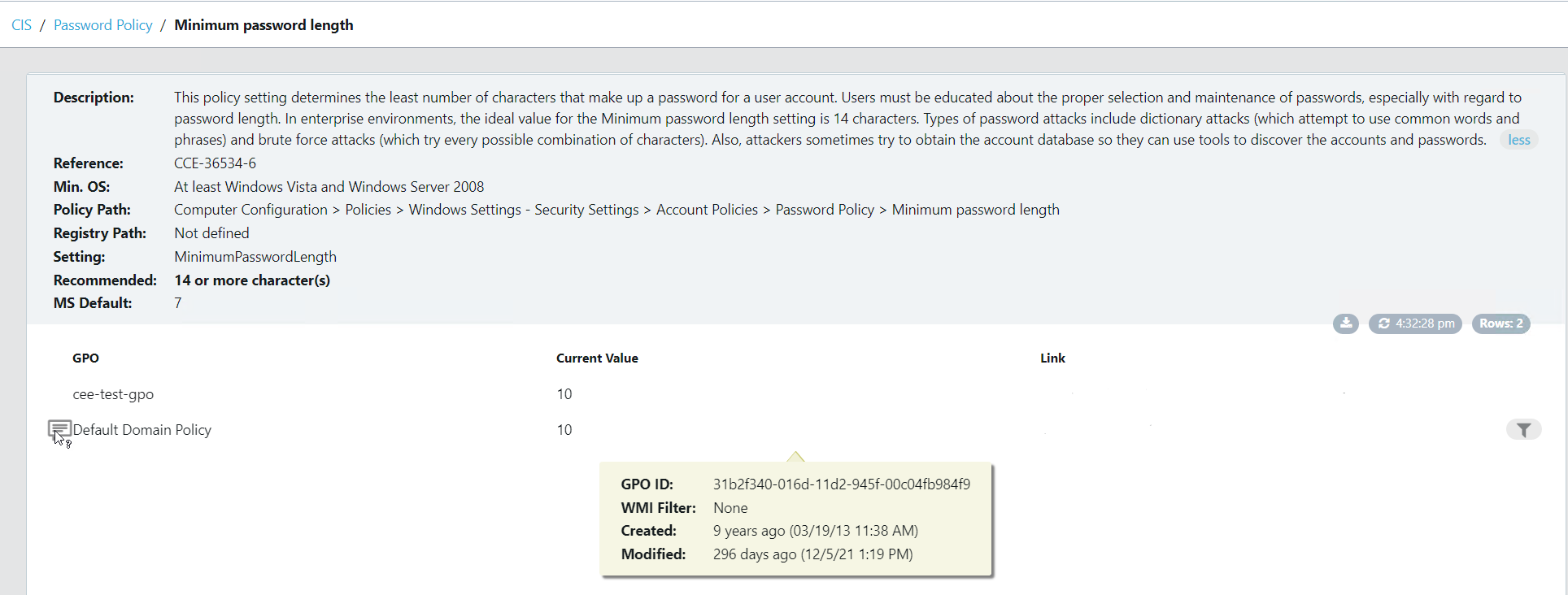
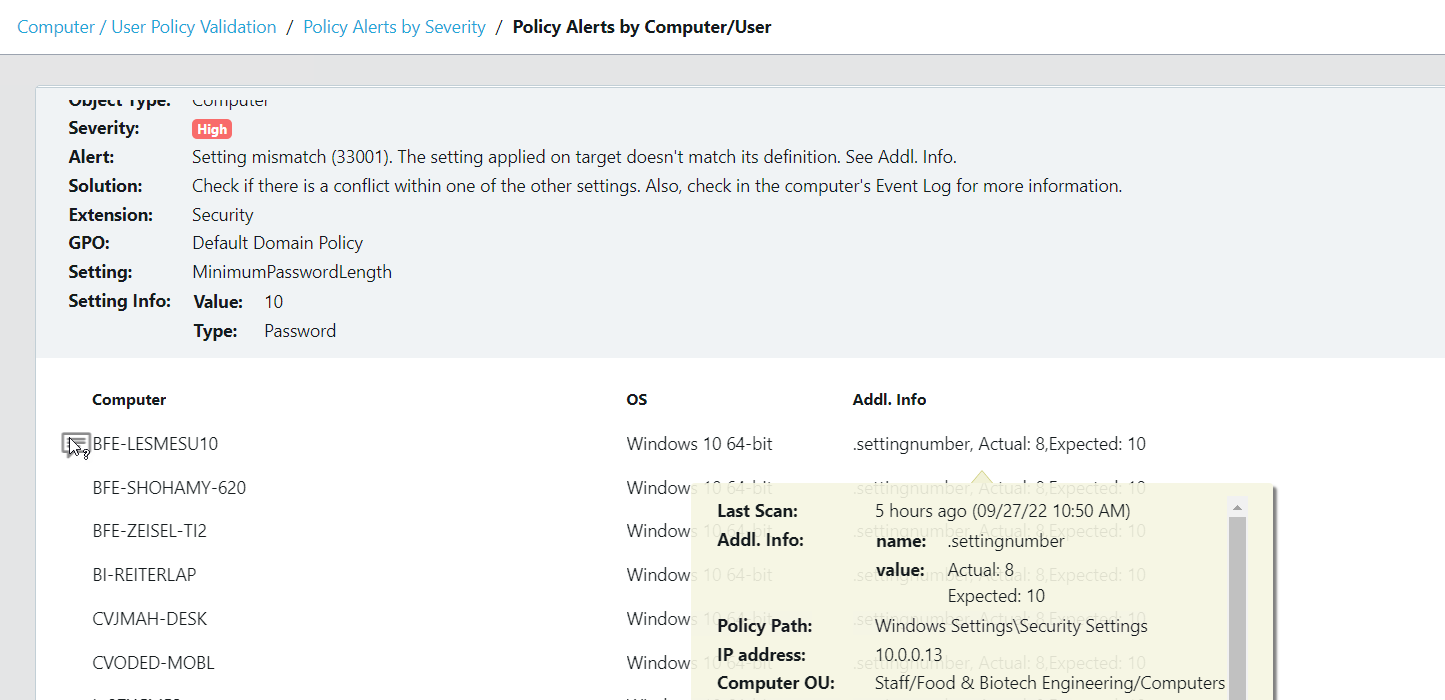
Take a look at the screenshots in the gallery below, I have taken these from the Armadillo test lab. You can see the reporting, the detail for any alert, and how to fix it. What impresses me the most without doubt is the reporting and dashboards because, from a single screen, I can see how big a problem I have, what the problems are, where they are, and how they map to the CIS benchmark.
Put it on your to-do list right now: this is a problem lurking in every single IT environment and goes overlooked, understated, and unaddressed. But not addressing it puts your business in that 80% bracket, which can be very expensive to recover from.