Most organisations have been successful to some extent in blocking malicious emails targeted at their employees. Various on-premise and cloud providers exist to take care of anti-spam, anti-virus, reputation scores and advanced features such as sandboxing of executables.
As a service provider with a list of blue-chip clients – we have been looking for a way to protect our clients from bad guys impersonating us by spoofing our email domain to phish for credentials. Until recently, organisations have washed their hands of this issue, putting the onus on end customers to educate themselves to identify and avoid clicking on malicious emails, but personally – I don’t think that is acceptable these days where a range of technical solutions are available to help you exercise a reasonable duty of care to your customers.
A number of open protocols have existed for some time to make things easier. DomainKeys Identified Mail (DKIM 2011)[1], Sender Policy Framework (SPF 2014)[2] and Domain-based Message Authentication, Reporting and Conformance (DMARC 2015)[3] can all help – but until now understanding and implementing these protocols has not been easy and organisations have not been willing to experiment with critical email systems.
At Armadillo, we evaluated a few services to help us to protect our customers from people spoofing our domains and decided on Agari. This blog documents our experiences so far in implementing these features. First order of business is to understand at a high level what these three protocols do, and how they work together.
- DKIM is a method of linking an email message with a domain name. As the domain owner, you can cryptographically sign messages using asymmetric keys such that the receiver can validate messages as being sent by the owner of the domain.
- SPF allows you to provide a list of the hosts which are allowed to send email on behalf of a particular domain – a whitelist of mail servers in effect.
- DMARC is the glue which binds it all together. Using DMARC allows you to say to a receiving mail server, “I use DKIM and SPF – if any messages from me don’t pass these checks, I would like you to reject them”. DMARC also allows the receiving mail servers to send back summary reports and forensic reports so you can check things are working as intended.
So, time to get to work! The first step is to turn on DMARC on your domain. The recommendation is to do this in what’s known a “p=none” mode. This turns on all the reporting features but without the risk of falsely blocking messages. To do this, it’s just a simple addition to your DNS record. This, and the Agari dashboard then gives some great pointers what to do next.
After enabling DMARC on my personal domain, I noticed a lot of dodgy stuff going on.
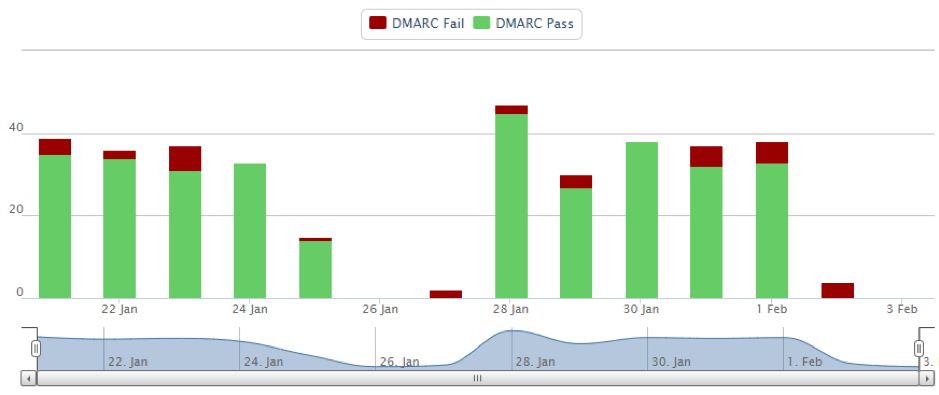
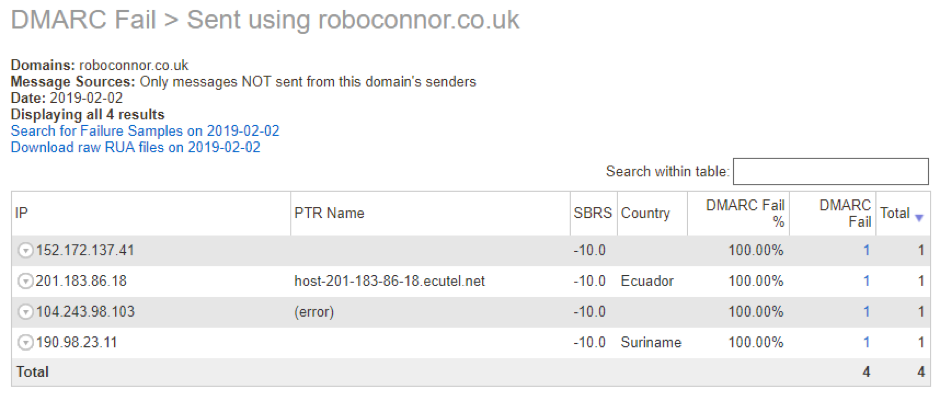
The only way my emails should be sent is via my gmail account. There is no valid reason for my emails to be sent from a server in Suriname or Ecuador. So, someone is spoofing my domain…
Thankfully, the wearearmadillo.com domain is spotlessly clean – however we saw some other legitimate domains in there we didn’t consider originally. Our ticketing system sends emails from our domain but from a different mail server, as well as the system we use for email marketing. Having DMARC enabled in monitoring mode allowed us to spot these and update our configuration without risking legitimate messages.
Updating the SPF record is really easy too – its another simple DNS record listing the authorised domains which you allow to send domains on your behalf. The Agari dashboard leads you through the process telling you the exact syntax to configure in your DNS provider. As an alternative, Agari hosted solutions also automate the process completely so you don’t have to make your own DNS changes. When Agari hosts the SPF record they completely take over the DMARC authentication process for all senders, including third-party ones. This is an alternative to using EasySPF to build your own record. It is an optional feature and organizations who don’t want to be locked into a given vendor can host their own. In this case, Agari assumes the responsibility of creating and hosting the SPF record, which is a critical step in the DMARC enforcement process. This means with a simple DNS change, companies are relieved from the burden of doing it themselves and ensured that the job is done correctly.
This week, we’ll be enabling DKIM on our Office 365 tenant which should complete the bulk of the configuration. We’ll then monitor the DMARC reports for a month or two – at which point we can switch the DMARC mode to “p=quarantine” which asks receiving mail servers to deliver possibly spoofed messages to spam folders, or directly to “p=reject” which just discards spoofed messages. With Agari’s hosted DKIM service, similar to SPF and DMARC records, organizations can choose to save the DNS management, infrastructure, and fulltime employee costs related to authentication by taking the DKIM management out of their environments.
While we could have done all this without using Agari – I’m not sure we would have managed it without unintentionally dropping legitimate messages, or we would have progressed along the journey so quickly. The tools provided by Agari to view failure samples and lead you through the process has been invaluable in getting us up to speed the current state of the art in email protection. With Agari’s hosted model, the entire process is fully automated, so customers don’t have to make any DNS changes themselves. Finally, the Agari platform adds another really useful feature to complete the jigsaw – the ability to check for lookalike domains. DKIM, SPF and DMARC work great to prevent people spoofing your real domain – but what about those sneaky targeted attacks where people register similar domains, perhaps swapping a ‘o’ for a ‘0’. Agari will alert us if any similar domains are registered, allowing us to warn our customers. In addition to alerting for these sneaky domains, Agari’s Advanced Threat Protection solution provides a proactive solution to stop lookalike (also known as cousin domains), and display name deception types of attacks that cannot be stopped with DMARC which is focused on same-domain spoofing.
If you would like any advice on how to protect your customers from email spoofing, Armadillo Managed Services can help you with a free proof of value with Agari. Please contact me directly if we can help.
Written by: Rob O’Connor, Chief Technology Officer at Armadillo.
[1] https://tools.ietf.org/html/rfc6376
[2] https://tools.ietf.org/html/rfc7208
[3] https://tools.ietf.org/html/rfc7489
[4] https://docs.microsoft.com/en-us/office365/securitycompliance/use-dkim-to-validate-outbound-email